Workato’s SOAR Accelerator can used for handling various types of security incidents:
- Handling Alerts Related to Malicious Network Traffic
- Protecting Endpoints
- Managing Vulnerabilities
- Stopping Phishing Attacks
- Managing SSL Certificates
- Investigating Failed User Logins
- Hunting Compromised Indicators
- Analyzing Malware
In the following example, we will see Slack Workbot in action as a triage layer for your organization capable of stopping phishing attacks before they infiltrate systems.
Business Scenario:
In this case, the Ingestion Recipe (Workflow) monitors a mailbox that receives emails reported as potential phishing emails by company employees.
When a phishing email is detected, it treats it as a security incident and sends it to the Slack triage layer first.
Case 1: Manual Investigation & Response

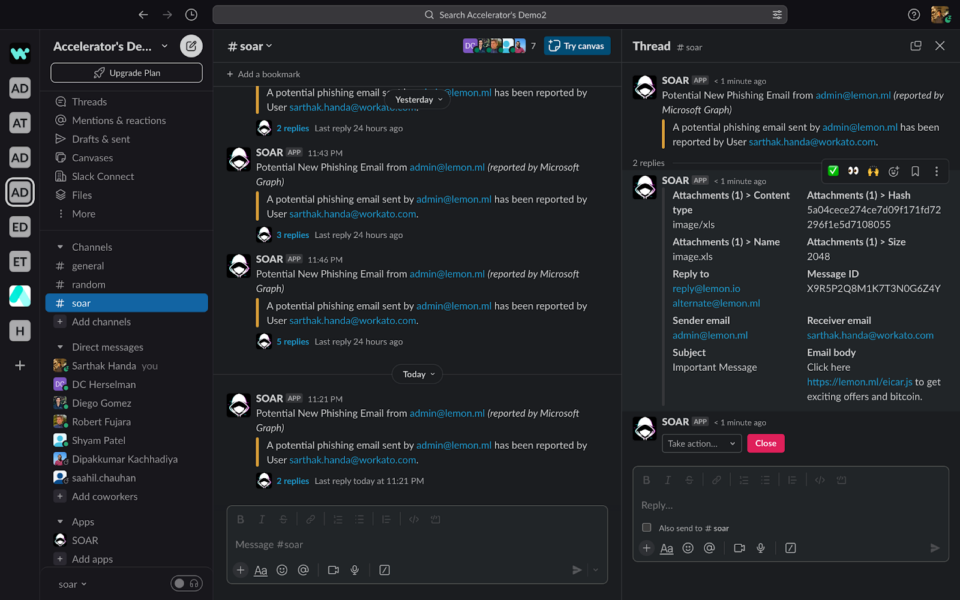
As the incident is ingested, you get a message on your Slack with the description of the Incident:

The incident details are attached to the message configured in the ingestion recipe. These fields can be helpful for the security analyst and security co-pilot to decide on actions and investigations.
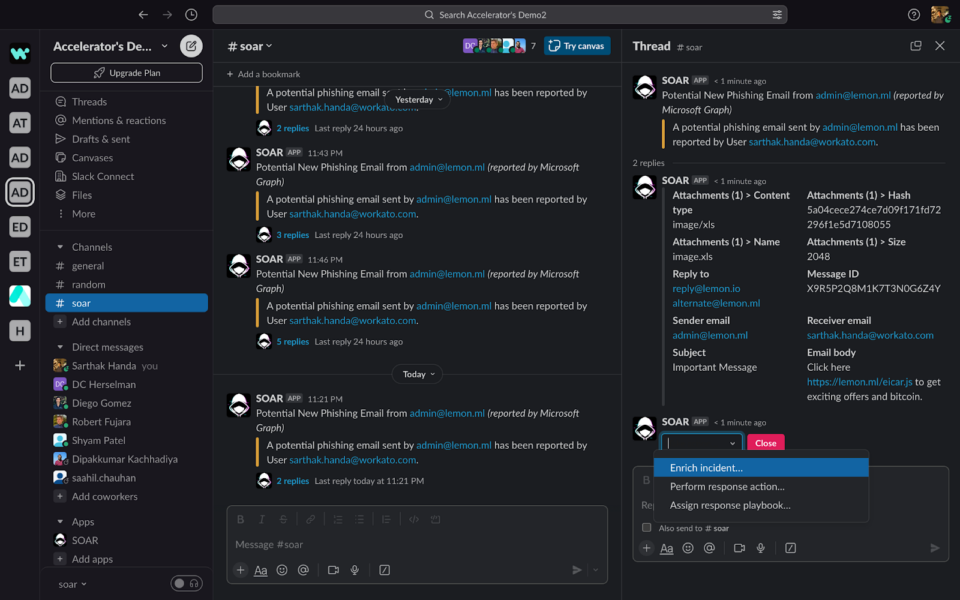
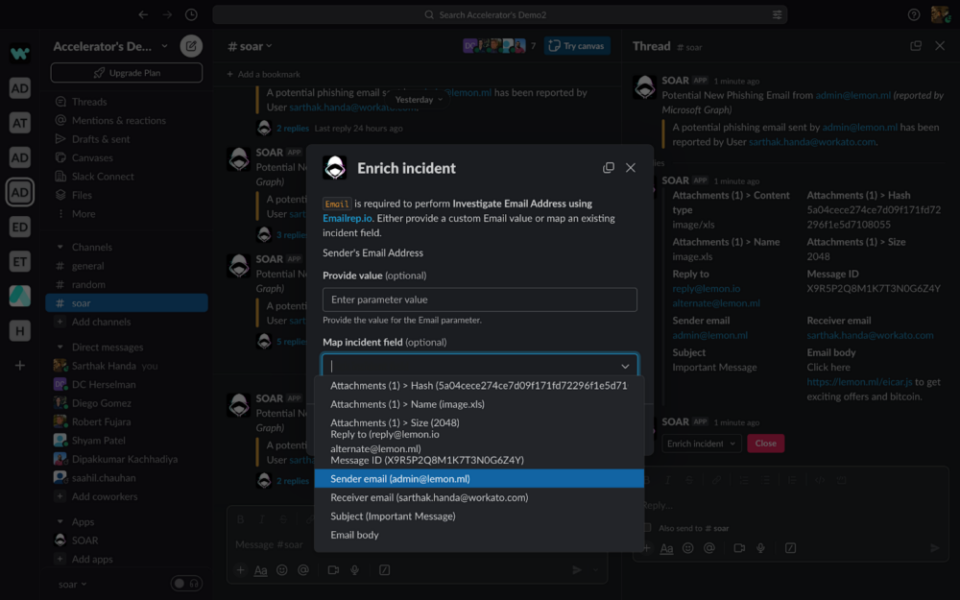
To run the investigation workflow called Enrichment Recipes in Workato, You can go to Take Action and select “Enrichment” from the drop down.
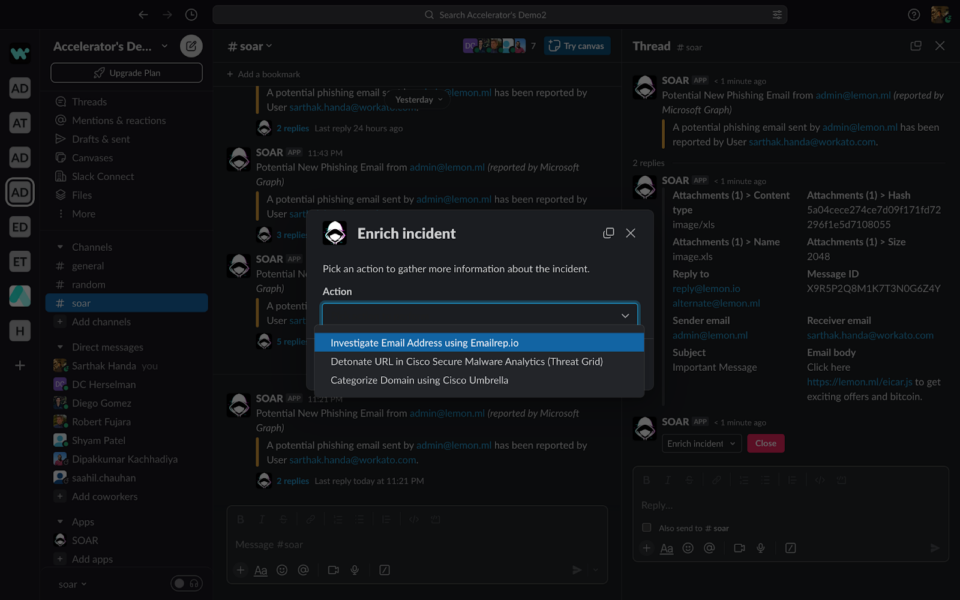
This will give you a pop-up with the list of all the available investigation steps with recipe descriptions. Select the action that you want to run.
Once you have selected the action, it will ask you to provide the value of the input parameters, if present. You can either pass the value by typing into the text box or, if the value is part of the Incident Fields, you can also select it from the drop-down
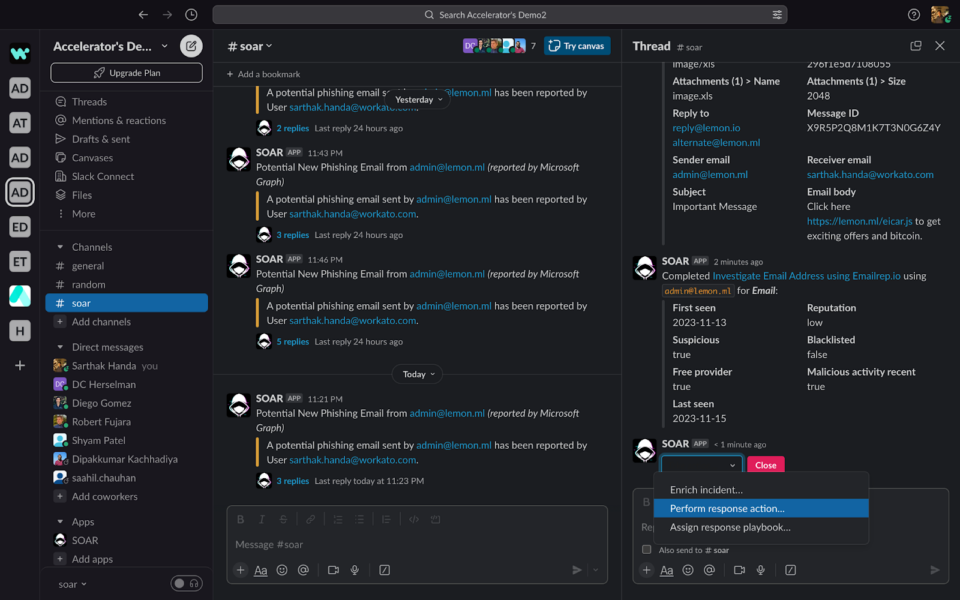
Once you confirm, it will run the workflow and post the output of the action in the thread message:

Similarly, we can run a response action or assign a prebuilt playbook to run for the given incident.
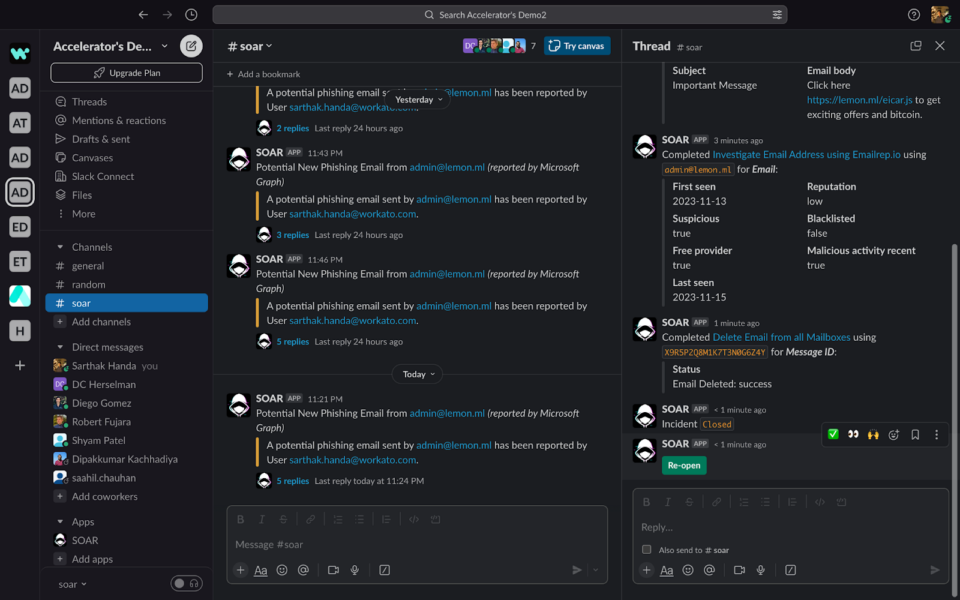
Once you have completed all the actions and you are confident that the incident has been handled appropriately, you can close the incident by clicking on the close button. This will give you a reopen button in case you need to reopen the incident if required.
So far, we have seen how to manually handle incidents using Workato’s solution via Slack Workbot. Manual handling is useful for the following use cases:
- Ad-hoc troubleshooting
- Leveraging domain knowledge
- Handling “unknown” incidents
- Making decisions as incidents occur
Next, we’ll examine how to automate your response.
Case 2: Automate using Pre-built Response Playbooks
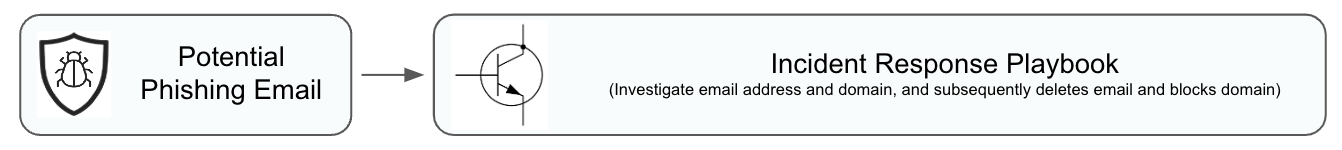
In this case, we will see the same incident being handled automatically by leveraging Workato Recipes as playbooks and rules-based auto assignment capabilities.
When you enable the Auto Assignment property, the SOAR solution will automatically try to find the right playbook or satisfy the conditions provided.
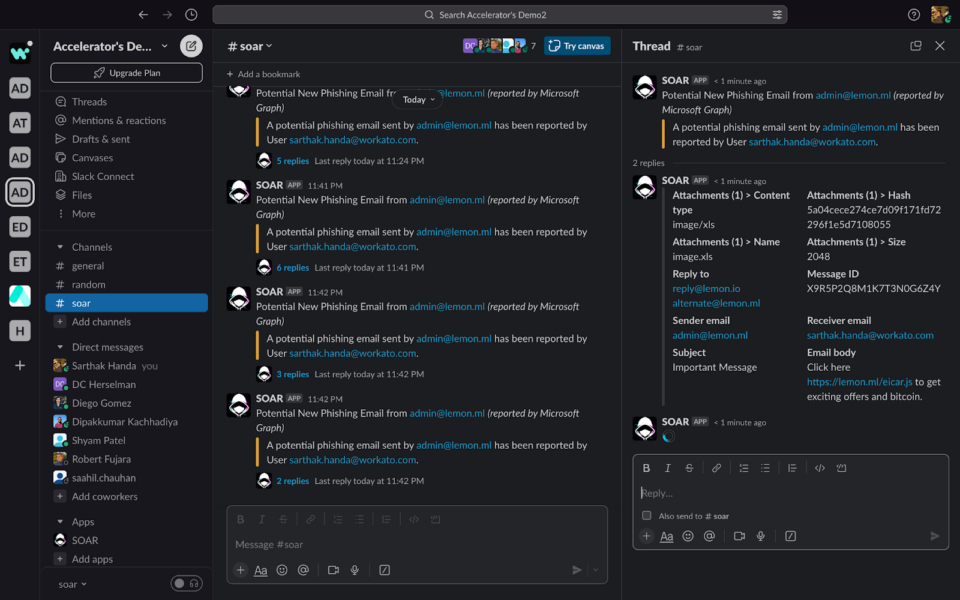
Once it finds the playbook, it will run it behind the scenes, giving you the following notifications:

As you can see, the incident, which took minutes to run manually, is now being handled within seconds.
Case 3: Scale using AI-powered Security Copilot

Workato’s Security Co-Pilot solution provides an AI assist for scaling responses to incidents.
If enabled, the Security Co-Pilot checks the incident description and fields, the available investigation steps and response actions recipes list as soon as the incident comes in. Security Co-Pilot can then recommend a workflow with a confidence score. If the score falls below a threshold set in the user configurations, the recommendation requires the security analyst to confirm. If the confidence score meets acceptable levels, the response runs automatically.
Below, you can see Security Co-Pilot is recommending an investigation step to run next, along with an explanation as to why.
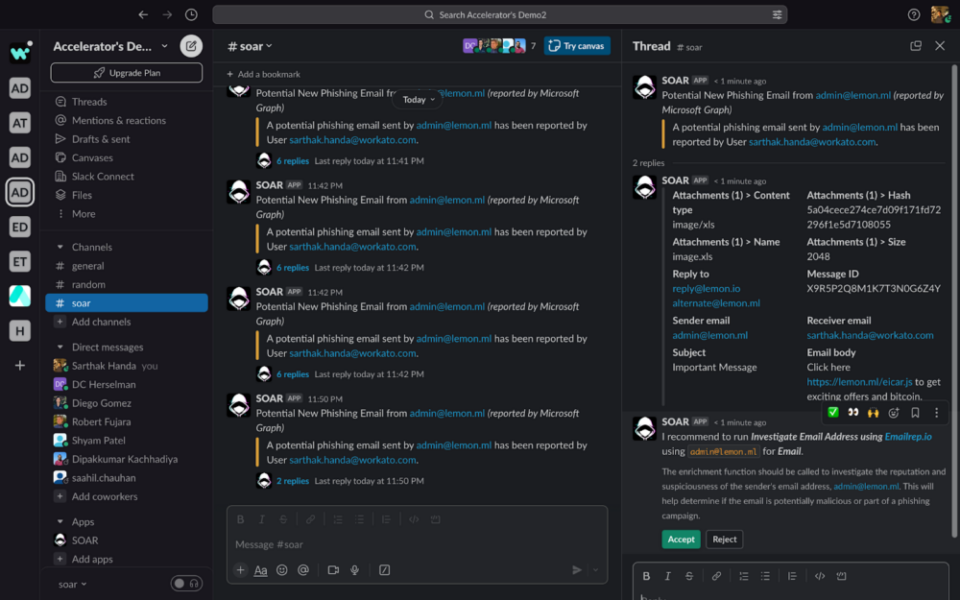
You can either accept the recommendation or reject it:
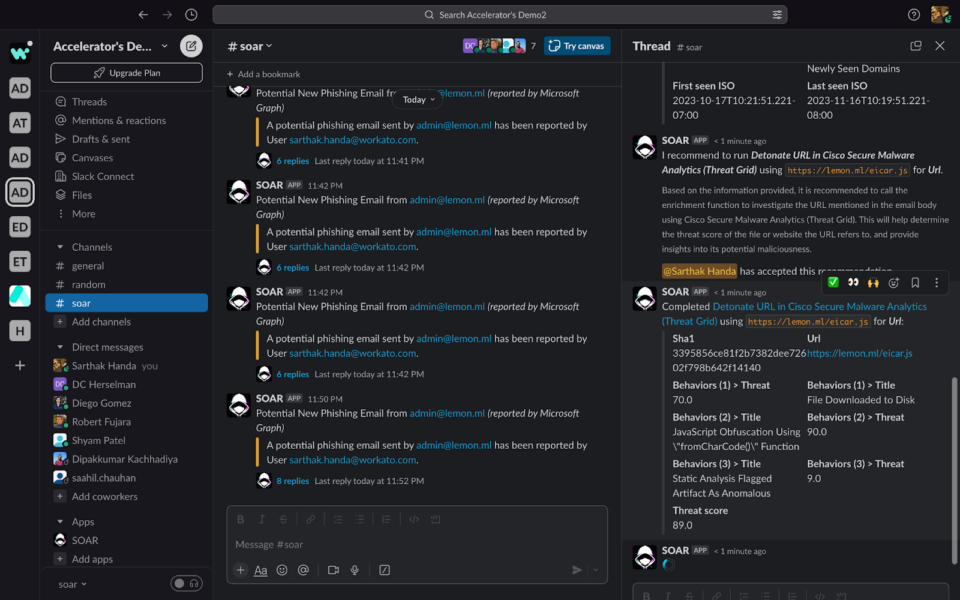
Once the Co-Pilot is confident to run the response, it will recommend the same to the security analyst:
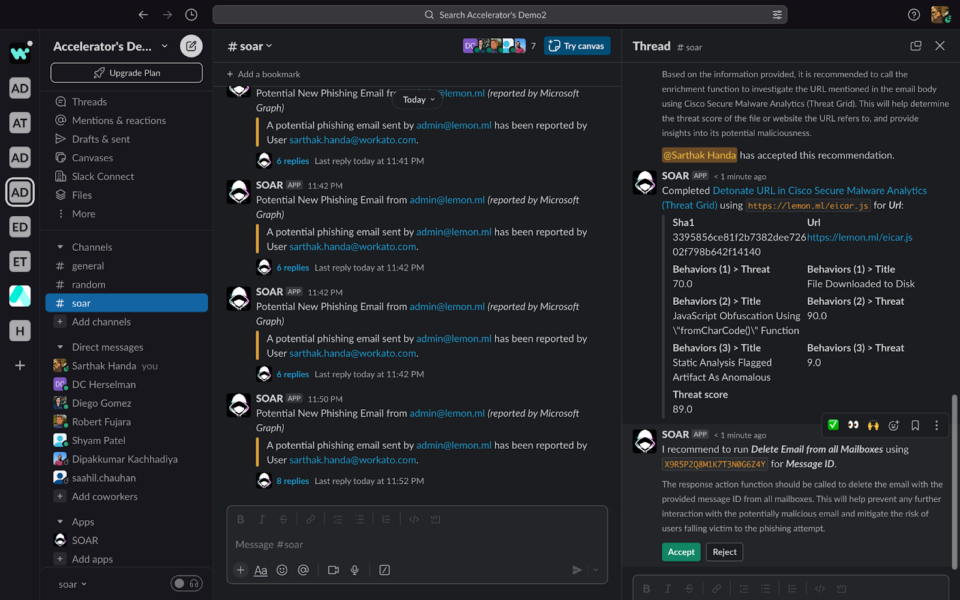
If no possible actions are required to run, the Security Co-Pilot will return a comment.
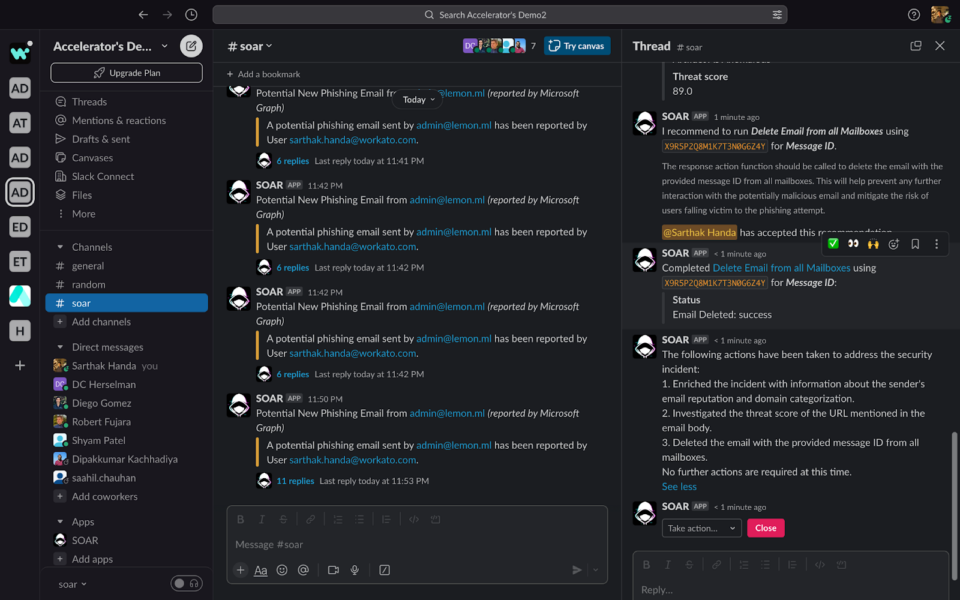
You can also comment on the thread to communicate directly with the Security Co-Pilot.
Security Co-Pilot showcases context-aware AI that provides actionable recommendations. When super confident, it automatically performs necessary steps and learns from expert decisions over time. Leveraging Security Co-Pilot’s AI capabilities opens up endless possibilities. As part of Workato’s SOAR Accelerator it enables organizations to respond promptly to threats, safeguard data, and ensure business continuity.