HashiCorp Vault secrets engine: Control secrets sprawl for your application connections
Update to our external secrets manager support
We’ve got some exciting news to share with you. Back in May 2022, we rolled out support for external secrets management using AWS Secrets Manager. It was a big step forward, but we didn’t stop there.
We’ve been listening closely to our customers, who have a wide range of security requirements. We understand that different organizations use different security tools based on their unique needs and policies. The demand for HashiCorp Vault has been consistently high, and we’re not surprised. It’s a popular choice among many of our customers.
That’s why we’re thrilled to announce that we now also support the HashiCorp Vault secrets engine!
Also read: Control secrets sprawl with AWS Secrets Manager support for your connections
First, let’s talk about secrets sprawl
If you ask any security expert what keeps them up at night, chances are secrets sprawl will be near the top of their list.
So, what exactly is secrets sprawl? Well, imagine a scenario where your organization’s precious secrets—passwords, encryption keys, access credentials, you name it—are scattered all over the place. They’re stored in various locations and apps, making it a real challenge to manage and secure them effectively.
Disadvantages of secrets sprawl: Why Centralization is key
Let’s talk about the downsides of secrets sprawl. When your organization’s secrets are scattered all over the place, applying reliable security policies becomes a real challenge. Even something as basic as password rotation turns into a daunting task, as you have to remember where all those passwords are stored in the first place. And here’s the kicker—secrets sprawl leads to increased attack surfaces.
Those stale, forgotten secrets lurking in the corners of your app ecosystem? They become juicy vulnerabilities for attackers to exploit. It’s not a situation you want to find yourself in.
That’s why many security teams prioritize centralizing their secrets management. When you can consolidate all your secrets in a single, secure location, developing and enforcing a strong and coherent security policy becomes a whole lot easier. That’s where external secrets managers, like HashiCorp Vault, come into play.
Platforms used for automating business processes, by nature, handle critical data from across your business systems, including sensitive functions like payroll. So, if you’re serious about centralizing your secrets management, your automation platform should be at the top of your priority list.
The good news is that now you have the option to store and manage your secrets using the HashiCorp Vault secrets engine. With Workato, you can effortlessly retrieve credentials whenever a connection is needed. It’s a game-changer that brings convenience, speed and security together.
So, let’s leave secrets sprawl behind and embrace a centralized approach to secrets management. By doing so, you’ll strengthen your security posture and gain peace of mind.challenge.
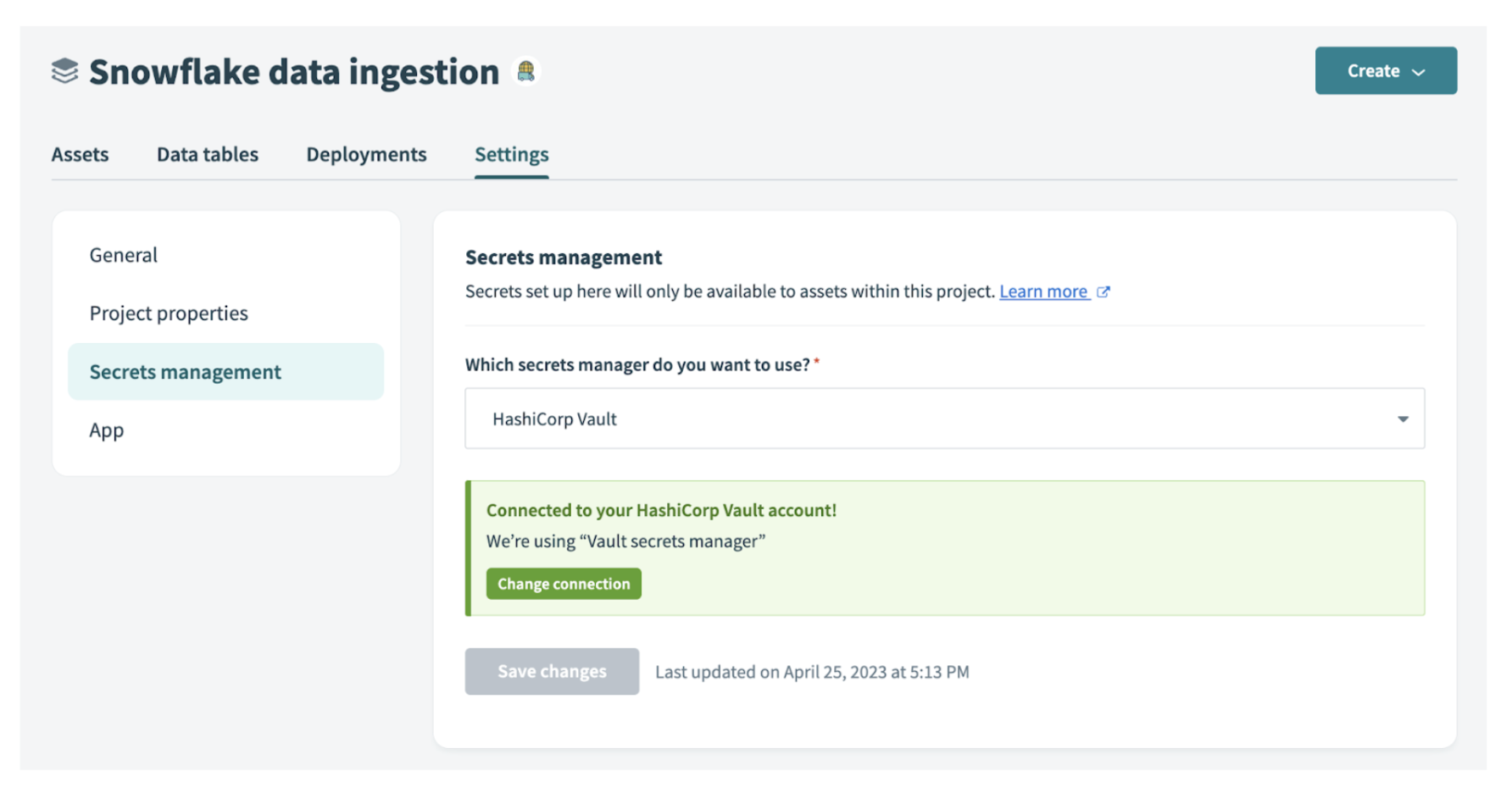
How to use HashiCorp Vault to create connections securely with Workato
By default, when you create a connection in Workato, you must supply your credentials, like username, passwords, or tokens, directly in the Workato UI. Workato stores the credentials, encrypted by a unique, connection-specific key.
With HashiCorp Vault secrets engine, you instead store your credentials inside HashiCorp Vault, and create a policy that allows Workato to access them. When you create the connection in Workato, instead of supplying the credentials themselves, you supply a reference to the credentials stored in the HashiCorp Vault secrets engine.
This means that Workato can connect to your apps and databases without actually storing your credentials at all.
Benefits of secrets management
Many of our customers require that credentials and secrets are not used directly in applications for security reasons. In most cases, the driving factor for external secrets manager use is the security or IT teams using centralized secrets management to control and protect the credentials from unauthorized access and distribution. Increasingly, we see demand for Workato to use credentials stored in a customer-managed secrets manager.
Secrets Protection
Storing your secrets only in a dedicated secrets manager helps protect your organization against potential compromise of credentials and connections. When you integrate with an external secrets manager like HashiCorp Vault secrets engine, your credentials are not stored in Workato at all.
Centralized secrets management
Centralized secrets management is the opposite of secrets sprawl. With all your secrets managed in one place it’s easy to create and enforce security policies such as policy-driven storage and encryption of credentials. It’s also simple to audit all access to your secrets over time.
Access control
Use of HashiCorp Vault to establish connections in Workato gives you more control over how and when those credentials can be accessed. You can revoke Workato’s permissions to access any secrets, at any time.
How does the HashiCorp Vault secrets engine work?
For detailed info on setting up the HashiCorp Vault secrets engine, see the HashiCorp docs.
HashiCorp Vault configuration
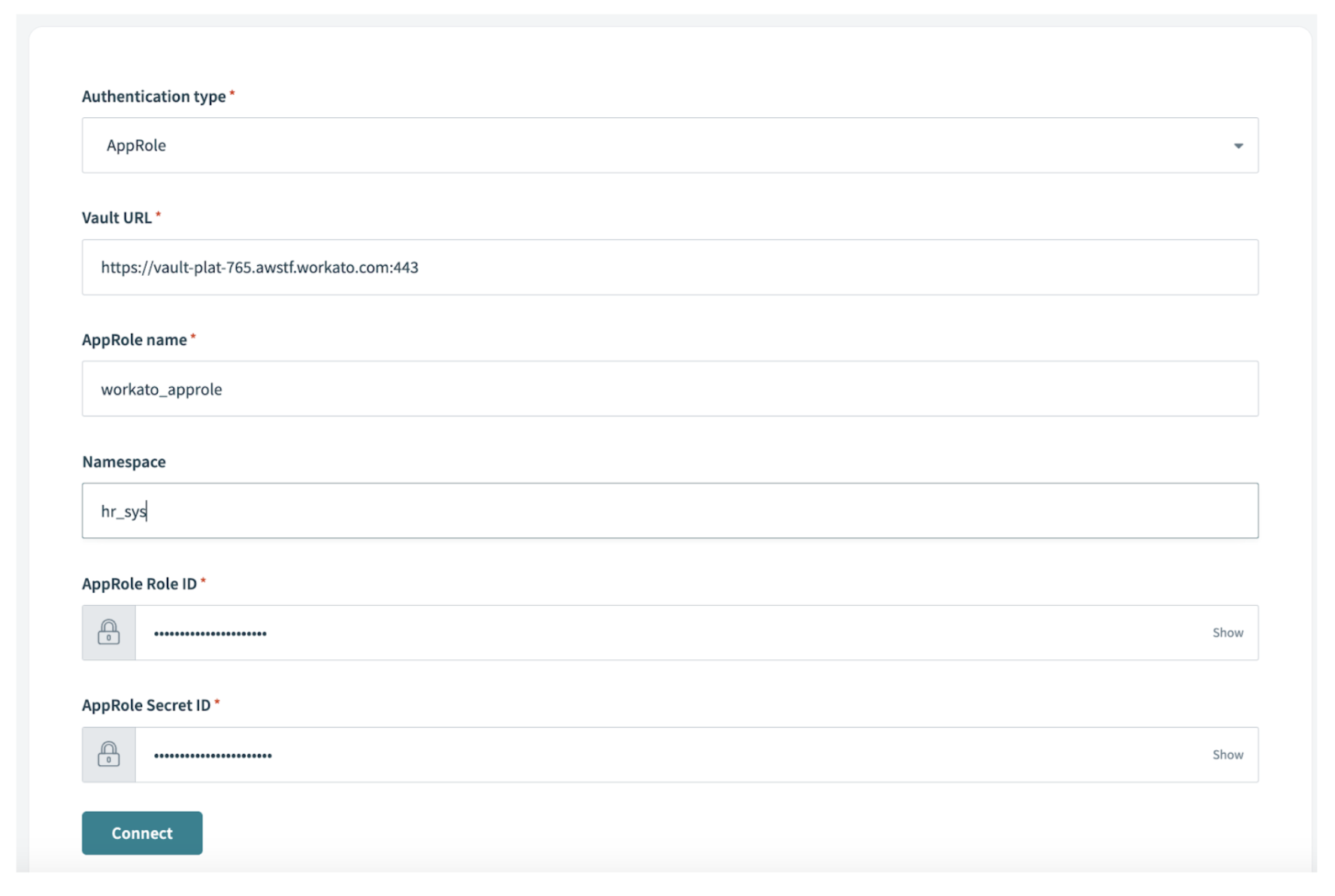
- Create an AppRole to grant access to the secrets engines in Vault. You can use multiple AppRole to control access to secrets based on the projects in which they are used. For example, you can create an AppRole for an order to cash automation that gives access to Netsuite and Salesforce credentials. AppRole must have “read” access to the secrets engine.
- Enable secrets engine in HashiCorp Vault. You can use multiple secrets engines to store project specific secrets. For example, you can create separate secrets engines for finance, marketing, sales, HR, IT etc.
- Create your credentials directly in the HashiCorp Vault secrets engine.
Workato configuration
- Create a HashiCorp Vault connection using the AppRole authentication.
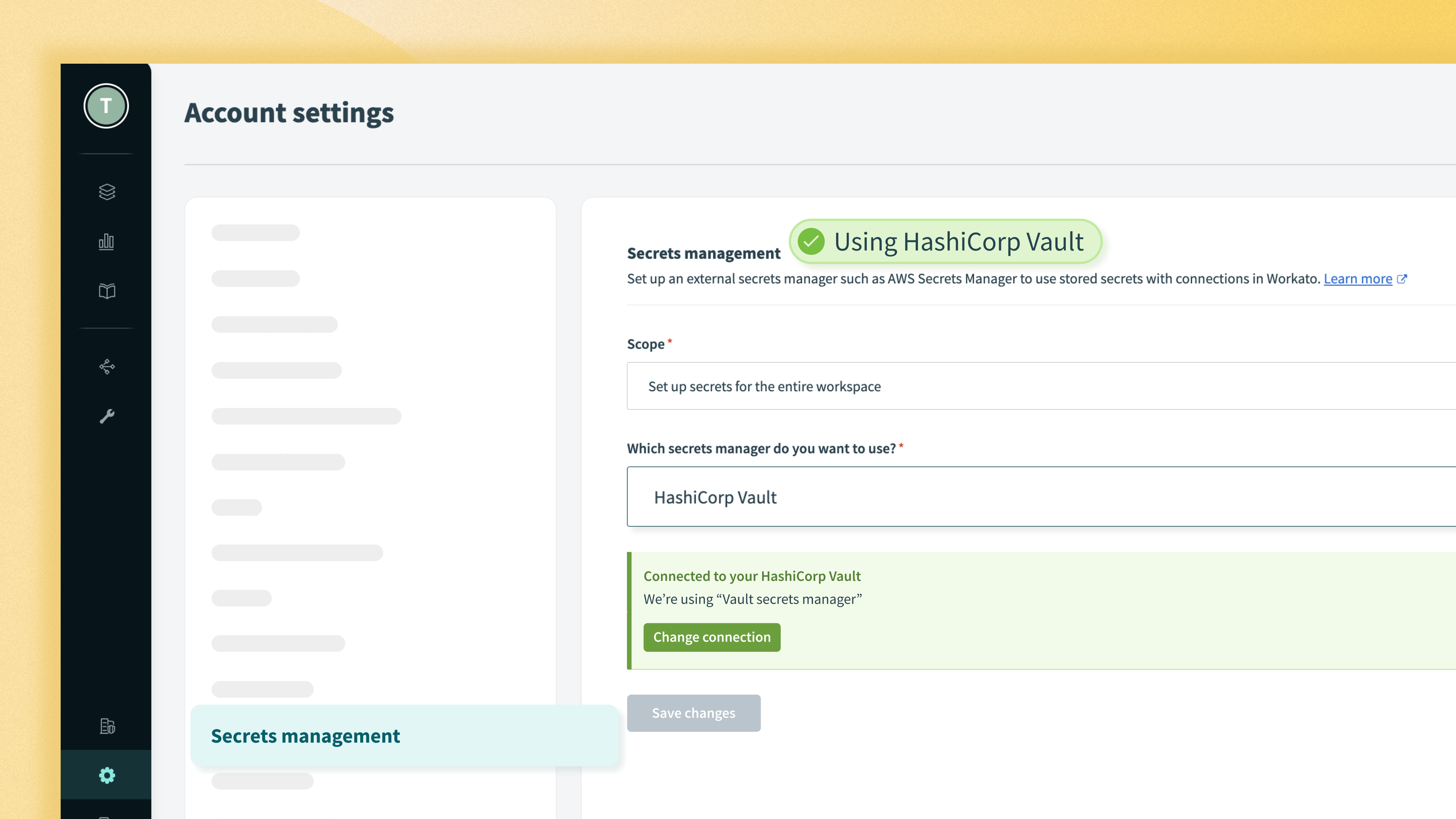
2. In the Secrets management configuration select the HashiCorp Vault connection.
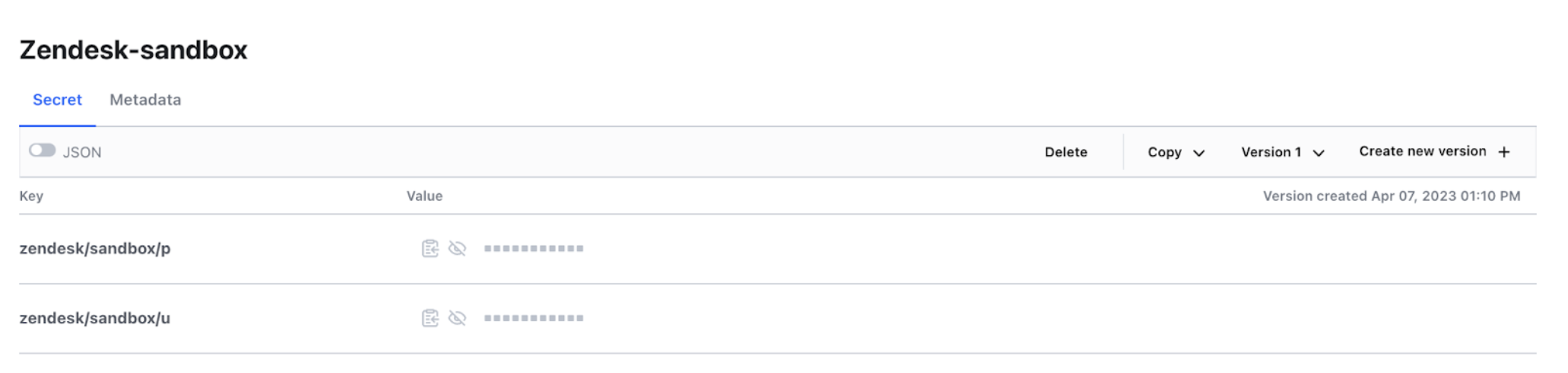
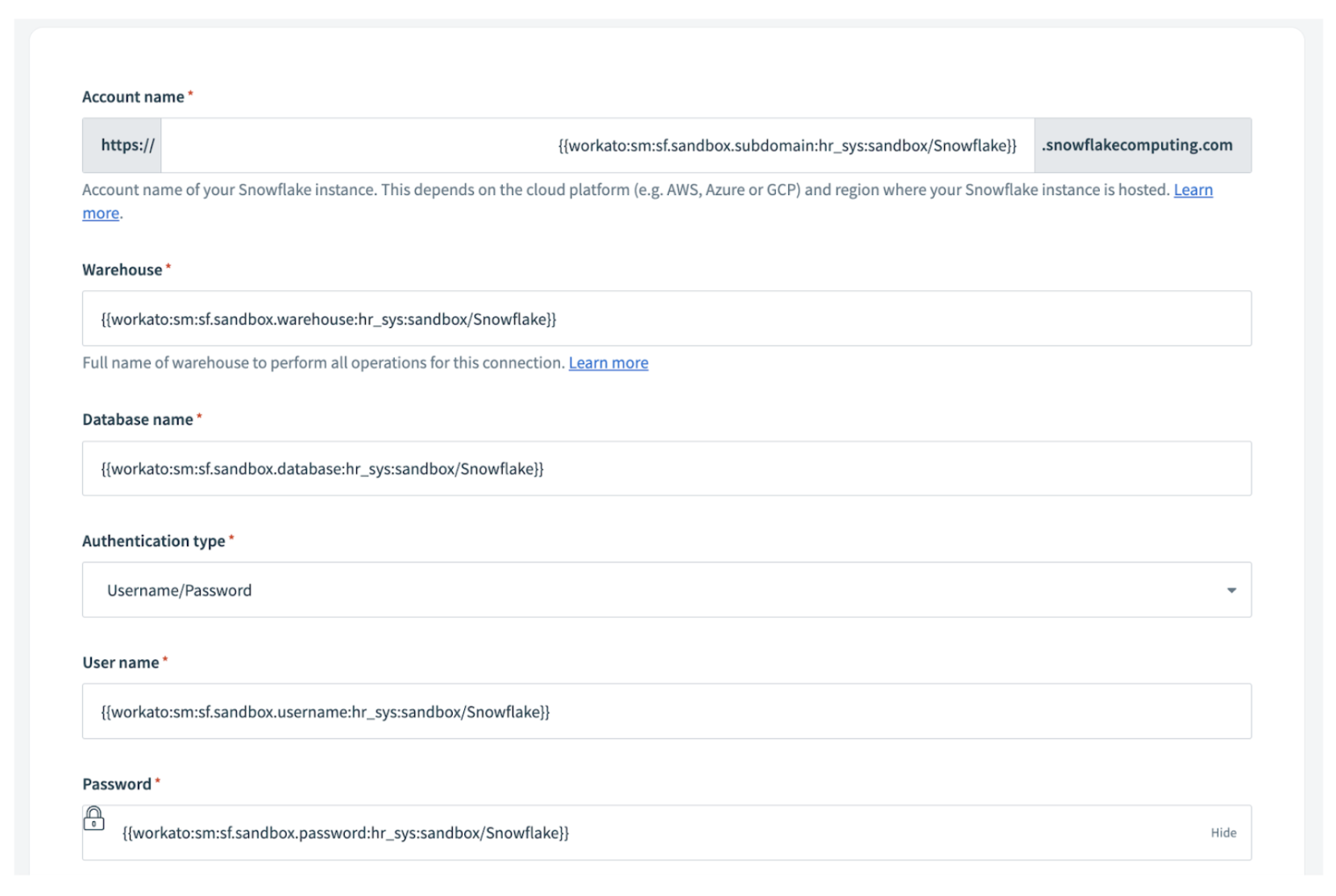
In any connection field that requires a secret, use the pre-defined format to reference the secret name that contains the secret value. The format is: {{workato:sm:<secrets key name>:<secrets engine name>:<secrets name>}}.
Example:
Secrets key name: sf.sandbox.password
Secrets engine name: hr_sys
Secrets name: sandbox/Snowflake
{{workato:sm:sf.sanbox.password:hr_sys:sandbox/Snowflake}}
FAQ about secrets managers
What secrets managers can I use?
The Workato external secrets manager currently supports Amazon Web Services Secrets Manager (AWS Secrets Manager) and now HashiCorp Vault. We are also adding support for Azure Key Vault in the future.
Can I use secrets in Workato via the secrets manager?
Yes absolutely! Workato’s external secrets manager support can retrieve the secret’s value as long as Workato has permission to access it and you’re using the right format. It can be actual secrets like username, password, API tokens. It can also be any other sensitive data that is required to successfully establish a connection to your application.
What happens when the administrator removes permission or deletes the secrets?
Once you remove Workato’s permission to access the secrets, the connection will no longer be valid after the cached secret expires. Jobs may fail as no valid connection exists to execute the step in the recipe.
What happens if I update the credentials in the secrets manager?
Once you update the secrets in the secrets manager, for each connection that uses the secrets, you must disconnect and reconnect to refresh the connection with the new credentials.
How can I automatically sync changes to credentials in the secrets manager with Workato?
Workato caches the connection for one hour to avoid calling the customer’s secrets manager too many times. To sync Workato to get the updated credentials, we will be introducing an API that invalidates the cache. Workato will get the latest credentials once the cache is empty. You can integrate with this API to automate synchronization with Workato whenever you change secrets in the secrets manager.