Azure Key Vault: a standout secret manager
Secure your secrets more seamlessly
In the era of automation and DevOps, organizations rely on agile, continuous integration and delivery to accelerate development cycles. However, with the increased automation of processes, the risk of inadvertently exposing sensitive credentials becomes a genuine concern.
Secrets management tools provide a centralized repository to securely store and manage secrets, such as:
- Passwords
- API keys
- Encryption keys
This facilitates the seamless integration of secrets into automated workflows, eliminating the need to hard-code credentials in scripts or configurations.
By seamlessly fitting into DevOps pipelines, secrets management tools bolster security and enable teams to focus on delivering innovative solutions without compromising sensitive data. That’s why we at Workato are always working to enhance our secrets management capabilities.
5 reasons why Azure Key Vault is a secrets management standout
The newest addition to our supported secrets managers, Azure Key Vault has been a standout for us and many of our users. Here’s why:
# 1: Centralized Secrets Management
Regardless of the automation or integration platform you are using, having a centralized secrets management system like Azure Key Vault simplifies the process of securely storing and retrieving sensitive information. This promotes consistency and reduces the risk of secrets being scattered across different systems or configurations.
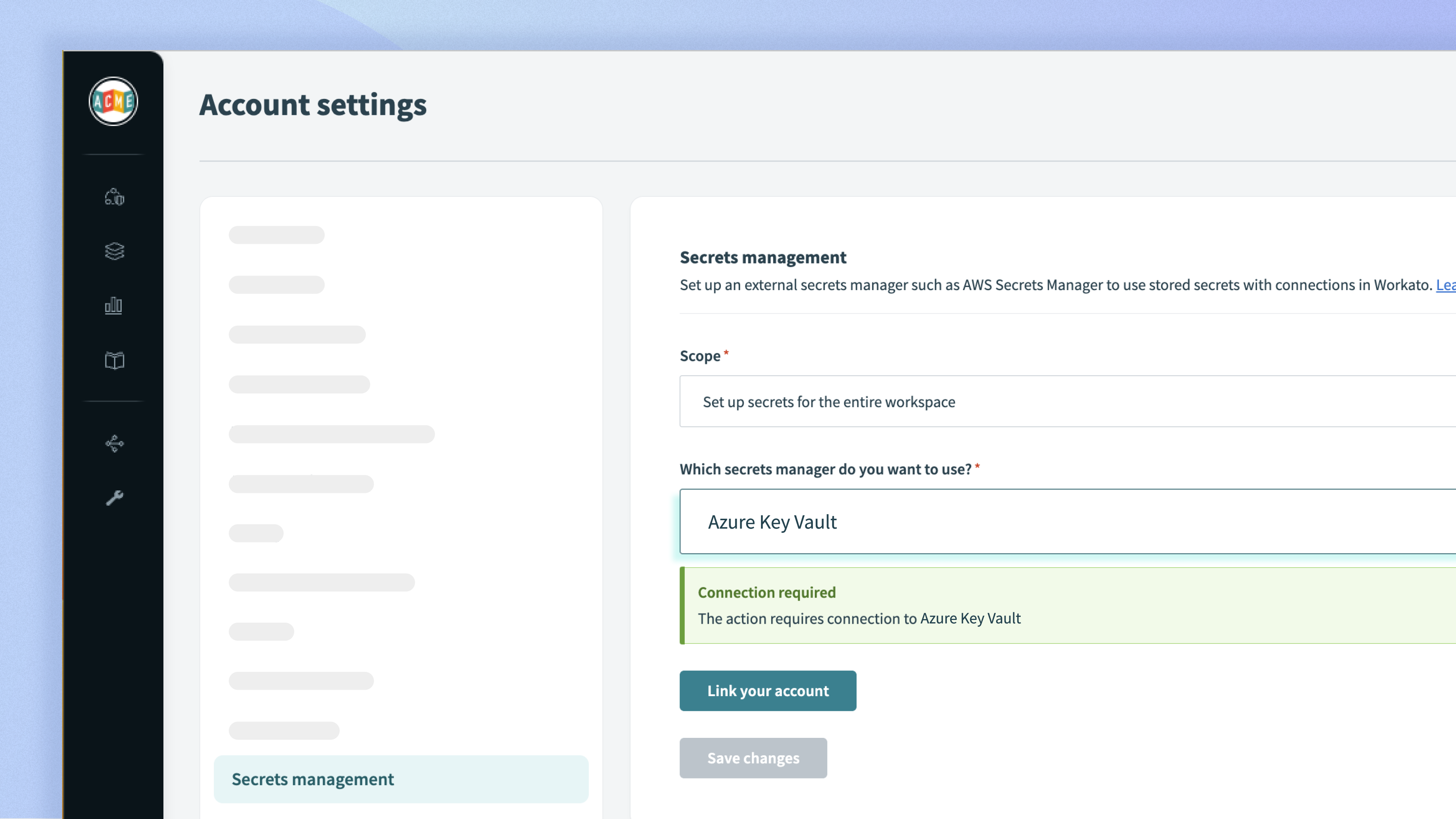
#2: Key Vault References
Azure Key Vault allows you to reference secrets securely stored in Key Vault directly, making this a handy feature when managing your Workato connection credentials.

In this example, we’re trying to establish a Zendesk connection. That’s why we’ve created a secret on Azure Key Vault and named it “zenDeskAPI”.
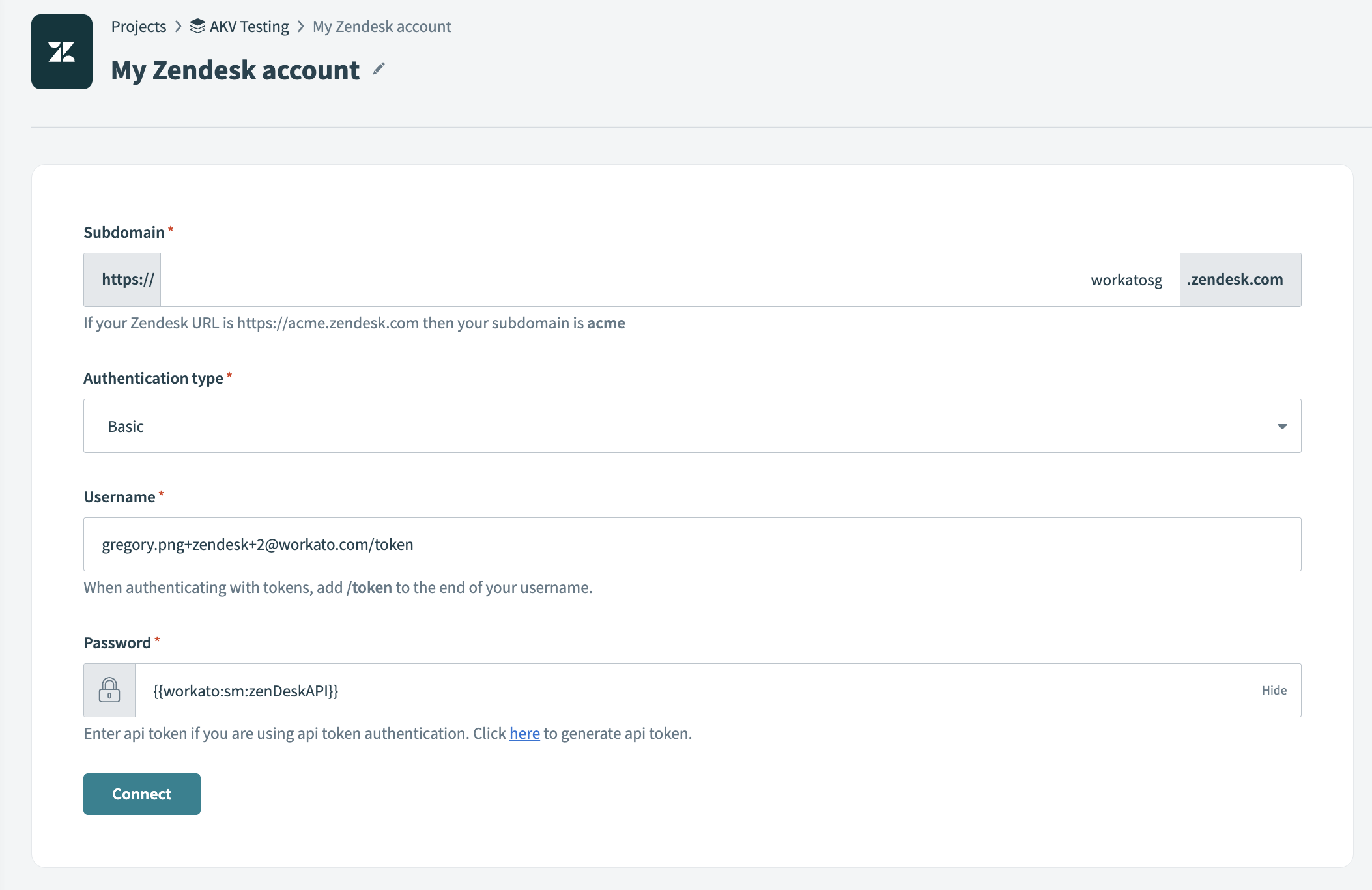
Then, we head to Workato’s connection page, and reference the same secret’s name in the password.
The password or API key in this instance will be “{{workato:sm:zenDeskAPI}}”.
#3: Secrets Rotation and Versioning
Automation and integration often involve the use of long-lived credentials or access keys. Azure Key Vault’s support for secrets rotation and versioning ensures that secrets can be regularly updated without causing disruptions to your automated processes. This removes the need to manually retrieve, enter, and update passwords on Workato!
#4: Security and Compliance
Azure Key Vault is designed with robust security features, including encryption at rest and in transit, access controls, and detailed auditing. When integrating with other platforms, the secrets remain protected, ensuring that sensitive data is not exposed inadvertently. This is especially crucial when dealing with compliance requirements.
#5: Standard APIs and SDKs
Azure Key Vault provides standard REST APIs and SDKs for various programming languages, making it easy to integrate with different automation or integration platforms. The availability of these APIs ensures smooth communication and interaction with Key Vault, regardless of the technology stack you are using.
Start managing your secrets with Azure Key Vault
Does your organization use Microsoft Azure? Find out the steps you need to take to start leveraging this powerful secrets management tool.
Frequently asked questions
What’s special about Azure Key Vault?
Azure Key Vault has added secret features and abilities to:
- Enable or disable a secret
- Set an activation or expiration date
- Limit public access to the vault by specifying an IP whitelist.
Moreover, since it’s part of the Azure ecosystem, you can easily access other resources such as Logic Apps and Event Grid.
Can I set up multiple Azure Key Vaults?
Absolutely! Simply configure it to be at a project level instead of a workspace level, so each project can have its own Azure Key Vault connection to multiple vaults.
What happens when I disable a secret that’s used in an active recipe?
After a secret is disabled and the “clear_cache” API is called, your active recipe will begin to fail since the connection will be invalid. The connection will become invalid even without calling the “clear_cache API” when the cached secret expires after 60 minutes.
Can I reference a secret that’s expired?
No, if your secret is past its expiry date, your attempt at configuring a connection will fail.
How can I automatically sync changes to credentials in the secrets manager with Workato?
To sync credential changes, simply clear your secrets management cache with the “clear_cache” API, so Workato gets the latest secret the next time it needs it. This means there’s no need for you to manually disconnect or connect again for refreshed credentials to take effect.
How can I automatically rotate my secrets as they approach expiry?
Since Azure Key Vault is part of the Azure ecosystem, you can either:
- Configure Event Grid to trigger a Function App that generates a random password whenever any secret is about to expire in your key vault, or
- Configure the Function App to send you a reminder email that a secret is about to expire
Read the official Azure guide for more.
Read about other secret managers we support
Control secrets sprawl with AWS Secrets Manager support for your connections
HashiCorp Vault secrets engine: Control secrets sprawl for your application connections