Security Spotlight: Workato’s InfoSec dominance: 6 Key Insights from the IRAP Assessment

Completion of Rigorous Assessment reinforces Workato’s Position as a Trusted Partner for the Australian Public Sector and Regulated Industries.
In GigaOm Research’s in-depth and independent evaluation led by practitioner analysts, Workato scored 95.2% overall for data security and governance, far surpassing peers.
This article dives into why Workato’s Enterprise Orchestration Platform has been described as being “more comprehensive and robust” from a security standpoint, earning a string of distinctions like the PCI DSS 4.0 Level 1, ISO 27001, ISO 27701, and most recently completing the InfoSec Registered Assessors Program (IRAP) assessment in Australia.
This has much to do with how Workato offers advanced enterprise-grade features “out-of-the-box” – baked in by default from the get go, not bolted on or left to developers to figure out for themselves. Below, we spotlight 6 differentiating features that assure some of the world’s most security-conscious organisations to trust Workato with their data: Data Residency, Data Masking, Custom Data Retention, Enterprise Key Management, External Secrets Manager, and Virtual Private Workato (VPW).
1. Robust Data Residency Options with Geographic Data Isolation
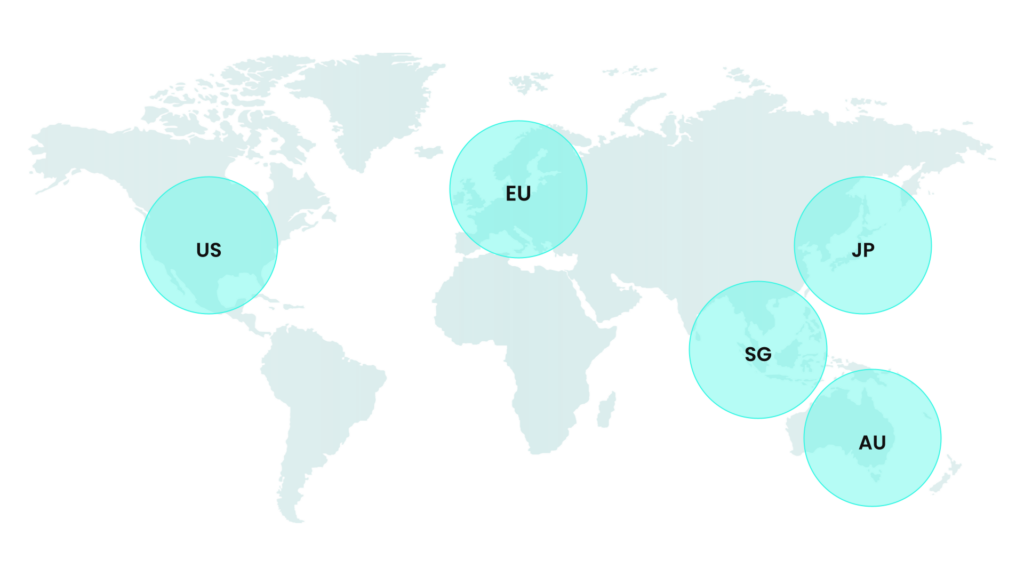
Several organisations need to comply with regulations that dictate where their data should be stored and processed. Workato’s robust data residency options allow customers like the Aged Care Quality & Safety Commission to manage their data within specific geographic boundaries, in full compliance with regulations. This is underpinned by Workato’s policy of not sharing data across data centres. Unlike other vendors, Workato fully isolates data to stay within specific regions, ensuring that sensitive information remains within the designated geographic area. This minimises data breaches and unauthorised access, particularly for regulated industries like government, finance and healthcare
A current look at where Workato’s data centres are located.
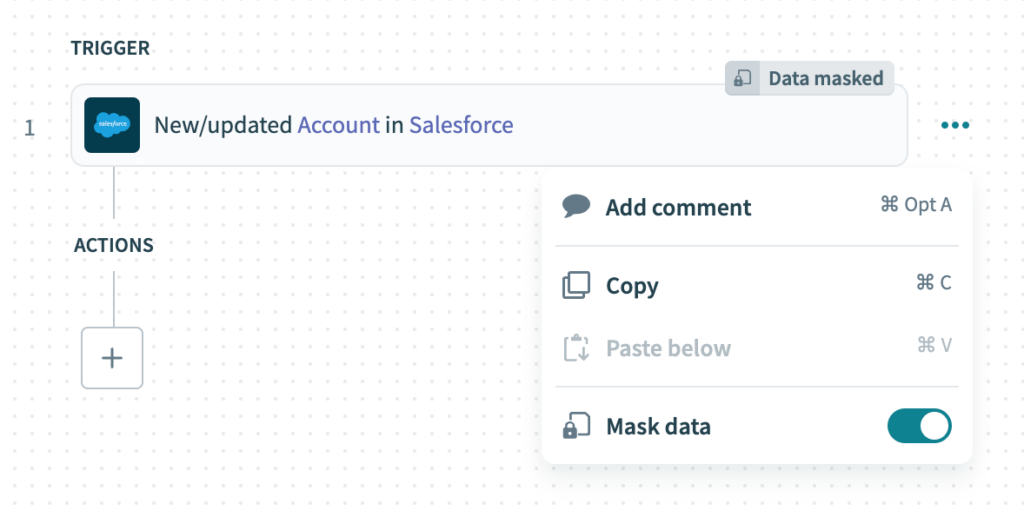
2. Data Masking Protects Sensitive Data
Data masking is a powerful technique that safeguards sensitive information by making it accessible only to authorised personnel. With Workato, organisations can seamlessly mask sensitive data within workflows, preventing unauthorised access and accidental exposure. Here’s a snapshot of how a user can mask data, to hide both input and output data from job reports and audit logs:
This feature is crucial for industries like financial services and healthcare, where protecting personal and financial data is essential. By ensuring data remains secure, Workato helps businesses comply with regulations such as GDPR and HIPAA, while maintaining data integrity and confidentiality.
3. Custom Data Retention for Enhanced Compliance
Custom data retention policies empower organisations to manage data lifecycles according to specific regulatory and business needs. With Workato, companies like Broadcom can define flexible retention periods, ensuring data is stored only as long as necessary before automatic deletion. Tailored retention policies allow organisations to comply with data retention regulations, reduce security risks, and maintain clean and efficient data management systems.This in turn minimises data breaches and streamlines operations. For more details on Workato’s data retention capabilities, refer to Workato’s Data Retention Documentation.
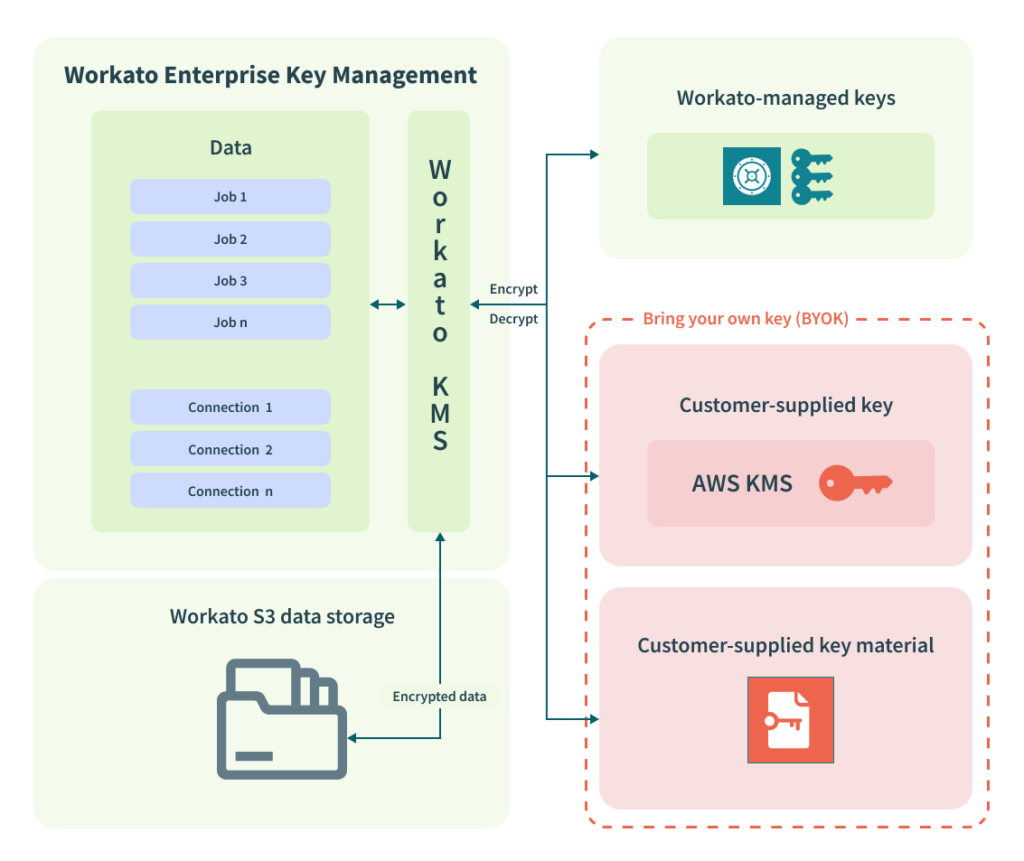
4. Enterprise Key Management with BYOK
Enterprise Key Management (EKM) is a crucial feature for security-conscious organisations like Atlassian and Canva, seeking advanced control over encryption keys used to protect their data. Workato’s EKM allows customers to bring their own encryption keys (BYOK), granting full control over the key lifecycle and the ability to manage encryption keys according to their internal security policies. This capability is essential for highly regulated industries, ensuring compliance with stringent security standards. By enabling the use of custom encryption keys, Workato empowers organisations to enhance data protection and trust in their security infrastructure. Refer to Workato’s EKM Documentation for more details.
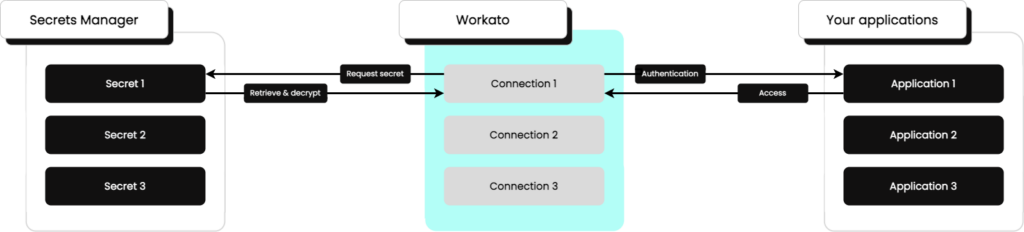
5. External Secrets Manager (SM) Streamlines Credential Management
Integrating an External Secrets Manager with Workato empowers organisations like Canva to securely manage and retrieve sensitive credentials for automated workflows. This External Secrets Manager stores secrets like API keys, passwords and certificates in a secure vault, and only allows authorised access. Workato’s integration with SMs like AWS Secrets Manager guarantees secure credential retrieval, minimising the risk of exposure or misuse. This integration is vital for organisations handling sensitive information, providing an extra layer of security and simplifying secrets management across diverse environments. Refer here for details.
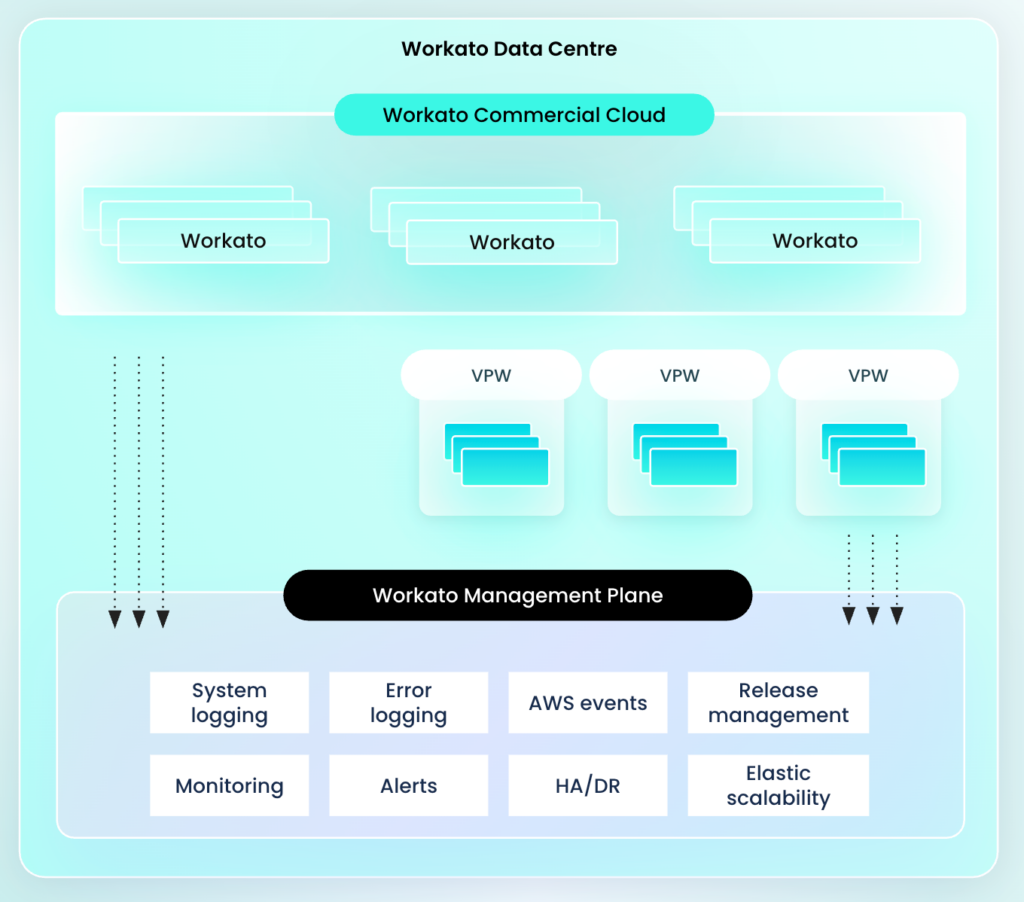
6. Virtual Private Workato (VPW) for a Controlled Automation Environment
Virtual Private Workato (VPW) offers a private deployment option for organisations who require enhanced isolation and control over their automation environment. VPW provides a dedicated and managed instance of the Workato platform within an AWS Virtual Private Cloud (VPC) tenant, ensuring complete workload and data isolation. This setup offers a higher degree of security and compliance, enabling organisations to meet stringent regulatory requirements and operate within a secure, controlled environment. VPW is ideal for businesses in regulated sectors such as government, finance, and healthcare.
Achieve excellence in security and compliance
Workato’s recent completion of the IRAP assessment process highlights our unwavering commitment to security and compliance, aligning with the stringent standards of the Australian Government. This achievement solidifies Workato’s position as a trusted partner for Enterprise Orchestration, empowering organizations in regulated sectors to confidently manage their data. With Workato, technology leaders can navigate the complexities of data security and compliance, ensuring secure and efficient operations. Collaborate with Workato to elevate your security posture and drive innovation at scale.