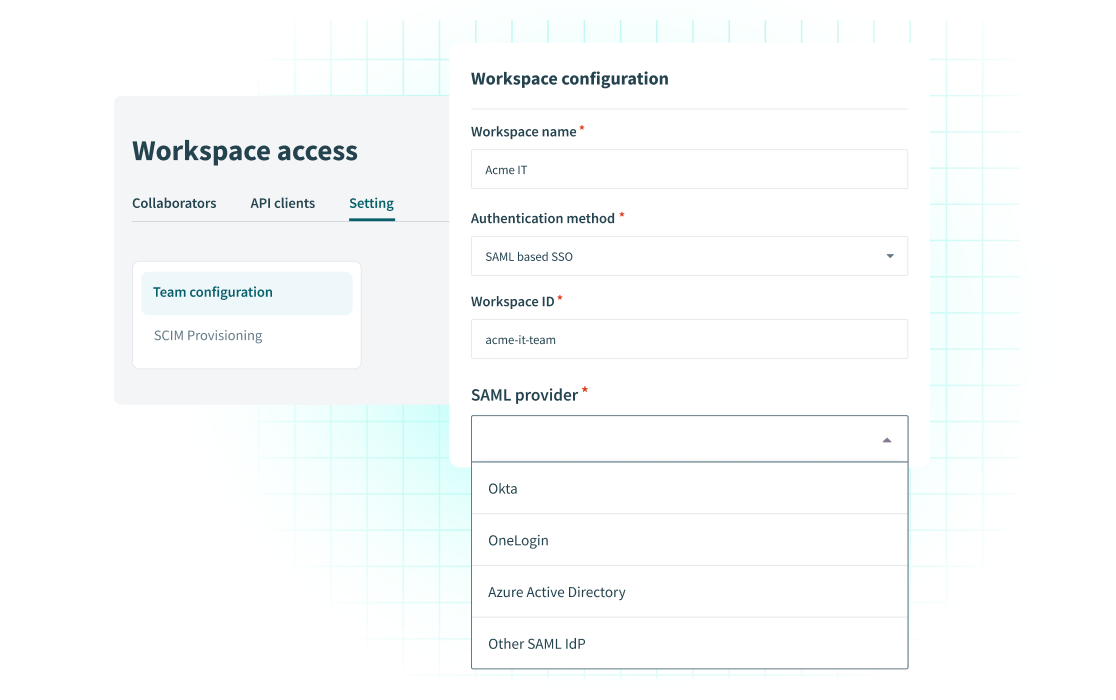
 User management
User managementFortify workspace access with SCIM, JIT provisioning and 2FA.
Prevent security threats, data loss and scale JIT user provisioning with SCIM and SSO/SAML
- SCIM user management
- SSO/SAML-based authentication
- Just-In-Time (JIT) provisioning
- Two-Factor Authentication (2FA)
- Session Security
- Account and User Management APIs
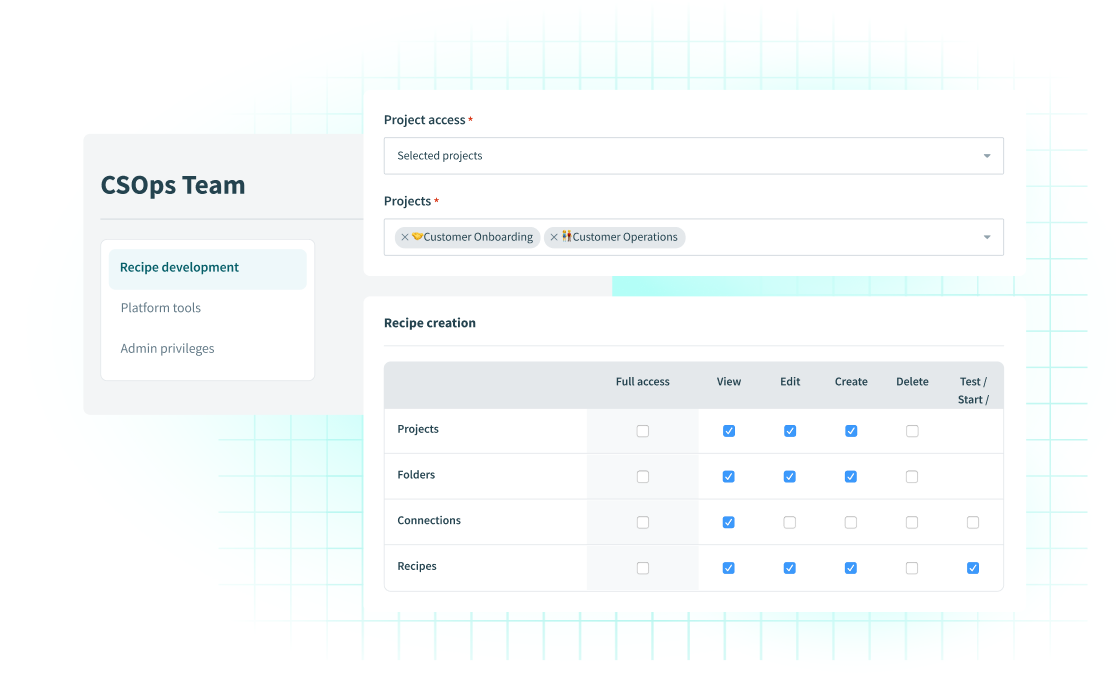 Governance
GovernanceAgile Governance and Auditing for Trustworthy Operations
Centrally provision and control all workspaces. Set your own policies for users with roles, and granular permissions
- Advanced RBAC
- AutomationHQ - Workspace federation
- Environment separation
- Sensitive data masking
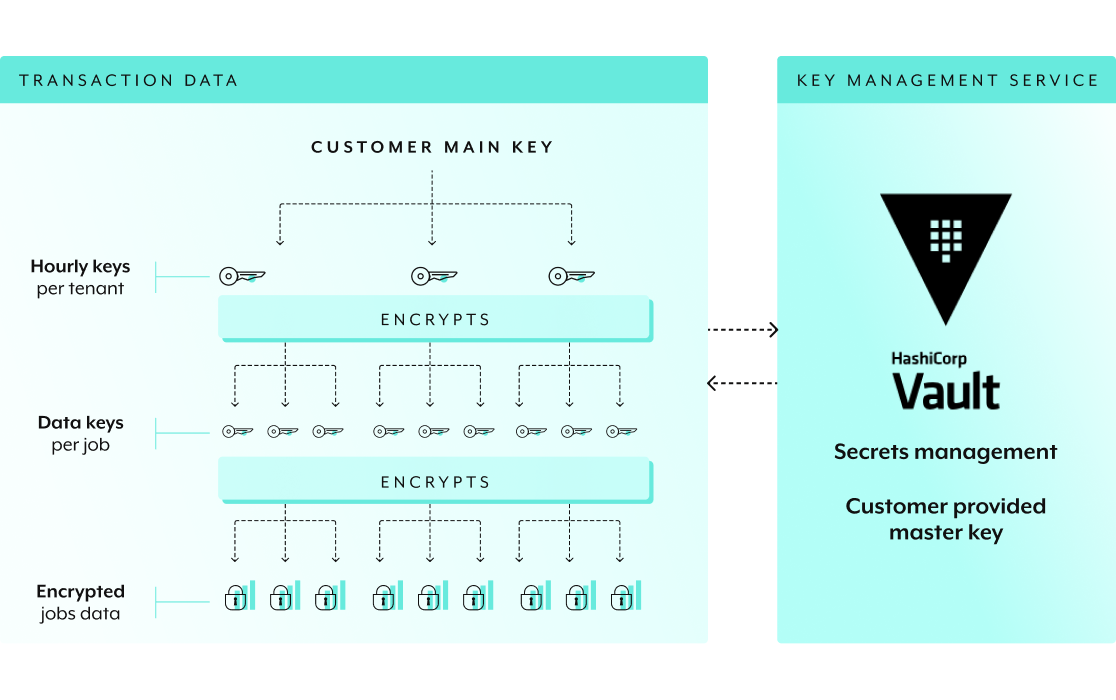 Data Security
Data SecuritySafeguarding Data within Every Automation Cycle
Gain total control over your data to meet critical compliance needs by using your own encryption key
- End-to-end data encryption
- Dedicated encryption key per account
- Hourly key rotation
- BYOK/EKM
- Secure Key vault (RAFT storage)
- Sensitive data detection and alerts
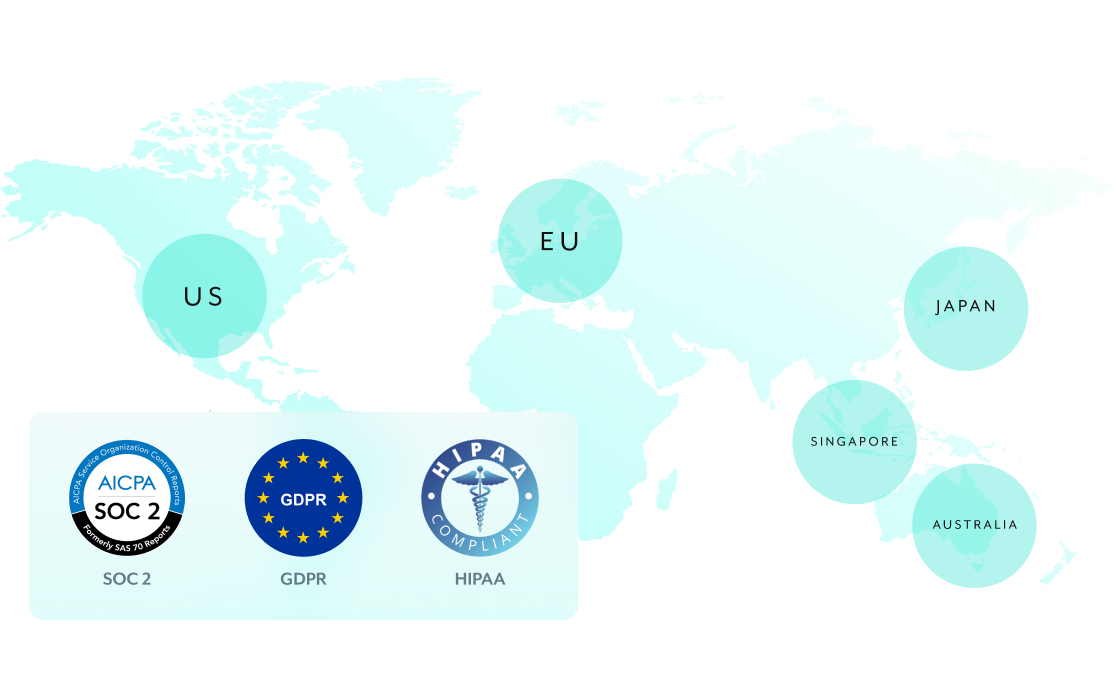 Compliance
ComplianceAutomate Confidently with Global Compliance Standards
Go beyond the industry certifications for compliance and privacy. Control data storage location and duration
- PCI-DSS Level 1
- ISO 27001
- ISO 27701
- SOC 3
- SOC 2 Type 2
- SOC 1 Type 2
- HIPAA
- Custom data retention
- Data masking
- GDPR compliant
- Regional data centers
- IRAP
 Product security
Product securityProtecting your work at every step everywhere
We take a security-by-design approach to safeguarding your data. The platform is built for high availability, scalability and security.
- Product access control
- Secure SDLC
- Vulnerability management
- Bug bounty programs
- 99.9% uptime
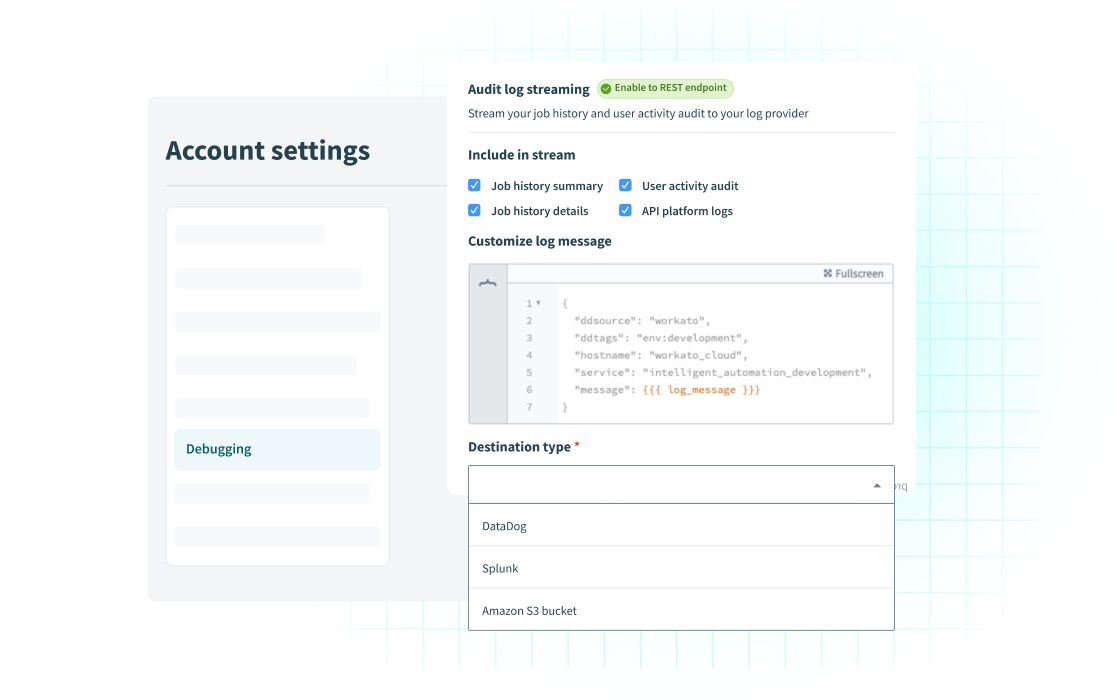 Audit and Monitoring
Audit and MonitoringAudit everything, miss nothing
Get unparalleled oversight by tracking every activity, and change. Stream logs to your favorite SIEM in real time for centralized monitoring
- Access logging and monitoring
- Activity audit log
- Job history audit
- Centralized logging service
- Audit log streaming
- Automate security audits and alerts
Security is our #1 priority
World-class and industry-leading security that sets new standards for keeping data safe.
